Top Cybersecurity Threats to Look Out For

Cyber Security Threat Prevention
While the internet brings convenience, it also makes your digital devices vulnerable to cyber security threats and risks. The top cybersecurity threats typically come in the form of viruses, spam and identity fraud. Cybersecurity challenges have become a major problem for organizations across industries around the globe.
While technology solutions can help enterprises protect themselves against these attacks, the most significant vulnerability in the network cannot be addressed by technology alone — employees themselves are susceptible when it comes to cybersecurity.
That is because social engineering attacks have grown in effectiveness, cost, and complexity. These types of attacks rely primarily on human psychology, using research to craft phishing emails that will fool employees into sharing data, passwords, and other information (as well as transferring files or money) without the need to execute malicious code on the user’s machine.
Unfortunately, that can make these attacks largely invisible to traditional security safeguards until it is too late.
Cyber Security Attacks by Industry
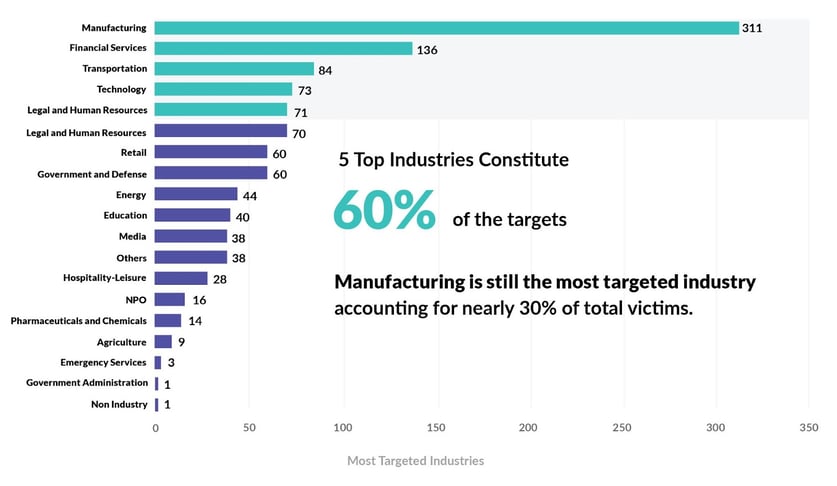
Cybersecurity is needed in every business industry. Cyberattacks could result in reputational and financial damage, regulatory penalties, business disruptions, and lawsuits. Fortunately, there are various preventative measures you can take to protect your organization against cyberattacks.
Read on for four of the top cybersecurity threats you should be aware of and how to prevent them.

1. Web-Based Threats: Phishing
Phishing refers to the process of trying to get confidential information by pretending to be a legitimate enquirer. Hackers and cybercriminals use various forms of communication, including emails, to reach unsuspecting individuals.
The emails often contain suspicious links, which lead to the installation of malware and access to sensitive information once clicked. Hackers are cunning, they create identical copies of legitimate pages to trick users into revealing their usernames and passwords.
To protect your personal and business data, you should be wary of official emails that request disclosure of personal data.
Other practical phishing prevention tips include:
- Updating IT equipment
- Investing in relevant cybersecurity software
- Verifying the legitimacy of suspicious emails and calls by contacting the companies before responding
- Not clicking links when unsure of the authenticity of a message

Phishing
Phishing is a social engineering tactic where an attacker sends fraudulent emails, claiming to be from a reputable and trusted source. For example, a social engineer may send an email that appears to come from a legitimate contact at your bank.
They could claim to have important information about your account but require you to reply with your full name, birth date, social security number and account number first so that they can verify your identity. Ultimately, the person emailing is not a bank employee; it's a person trying to steal private data.
Phishing is a common practice used by cybercriminals to steal personal data and login credentials, these phishing emails include several deceptive strategies:
- Blending malicious and harmless code to trick Exchange Online Protection (EOP).
- Incorporating legitimate links to evade detection (and rerouting to spam folders) by email filters.
- Stealing and modifying brand or organization logos.
- Sending emails with minimal written content.
- Using shortened URLs to trick Secure Email Gateways (SEGs) after an email arrives in a user’s inbox.

Spear Phishing
This is when extensive research is conducted when cyber criminals set their sights on a user. Using Google and social media platforms, the attacker can create a believable attack to fool the user.
Let’s say a user frequently posts their interests on social media as a member at their favorite store. The attacker can create a Spear Phishing email that appears to have come from that store. Victims are more likely to fall for this scam since they recognize the store as the supposed sender.

Whaling
Better known as the Moby Dick of phishing attacks. Rather than targeting an average user, social engineers focus on targeting higher value targets, such as owners, CEOs and CFOs. Whaling is a highly targeted phishing attack masquerading as a legitimate email. Whaling is digitally enabled fraud through social engineering, designed to encourage victims to perform a secondary action, such as initiating a wire transfer of funds.
Only a single employee has to fall for a phishing email for an attacker to gain access to your company's email.
Thus, it is essential for every business to take simple steps to reduce the risk of phishing and business email compromise:
- Security Awareness Training for staff.
- Two Factor Authentication on email accounts.
- Secure configuration of your email service.
How to Spot a Phishing Scam
Phishing attempts are getting more sophisticated in their methods and increasingly difficult to spot. If you keep an eye on what arrives in your inbox though, there are a few tell-tale signs to look out for. If you are the recipient of a suspicious-looking email, ask yourself these questions:
- Who sent it? Phishing emails often have suspicious-looking email addresses that are often different from the sender. You can find out the real email address by hovering your mouse over the sender’s name.
- Did you ask for the email? If you didn’t sign up for any service, chances are it could be a phishing scam.
- Are there unexpected attachments? You have to be especially careful if there are documents attached. It is likely to be an attempt to trick you into downloading malware on your device.
- Are you being asked for security information or personal details? Sometimes a company will ask you for personal details. They should not be asking for full passwords or pin numbers; all not secure in an email! This also applies to credit card details or login information.
- Is the message using urgent or threatening language? Phishing scammers know people procrastinate on emails and so they often ask you to act quickly (or now!) so that you don’t have time to think about it. Click now, pay the price later.
- Is the language used odd or does it contain errors? With more current phishing emails, company logos can look very accurate, but the wording can seem questionable. Look out for sentences that are spelt correctly but the grammar seems off, or as if it has been pasted in from translation software.
- Does it resemble other emails from this company? As we mentioned above, some phishing emails have gone to greater lengths copying the look of official emails. One example would be a set of PayPal scams that circulated recently, which had accurate copies of the company logo. If it looks phishy, check the email address carefully and again check to see if they are asking you for more details than you expected, such as information the company should already have on file.
How to Prevent Email Phishing
It would be very difficult to prevent all phishing messages from coming to you in the first place but there are some actions you can take to eliminate risk once they arrive. If you see something you suspect might be the work of cybercriminals, here are three actions to take:
- It's a good idea to delete the email or message straight away. Don’t forget to also flag it as ‘spam’ or ‘junk’ so your email provider can aim to filter out similar messages in future.
- Keep your security software up to date. This will often warn you of suspicious emails and emails; as well as tackling malware before any damage is done.
- Contact your financial institutions or organizations. Report any incidents quickly to your bank, credit card provider or mobile phone network.

2. App-Based Threats: Malware & Ransomware
What is Malware?
Malware is a broad term that refers to various malicious software variants. Malware is an intrusive software that is designed to damage and destroy computers and computer systems. The term Malware originates from “malicious software.” Cybercriminals, often referred to as hackers, steal data, damage and destroy computers and computer systems.
Malware threats are the most common forms of cyberattacks. Malware refers to malicious software installed in your systems when you click suspicious emails or links. It can self-replicate, obtain private information, limit your access to vital components of your system, and damage your units.
To prevent a malware attack, businesses should:
- Install anti-malware software.
- Backup crucial data and files in an offline location.
- Conduct regular system inspections and maintenance.
- Download software and files from trusted sources.
A growing wave of increasingly sophisticated ransomware attacks poses a threat to critical infrastructure and organizations around the world – and attacks will continue as long as victims keep giving in to ransom demands, a joint advisory by cybersecurity bodies in the US, UK and Australia has warned.
The advisory from the UK's National Cyber Security Centre (NCSC), Australian Cyber Security Centre (ACSC), Federal Bureau of Investigation (FBI), National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) has detailed the growing risk posed by ransomware and has urged businesses to take action to protect themselves from attacks.
The NCSC describes ransomware as "The biggest cyber threat facing the United Kingdom", with education one of the top targets of ransomware gangs, alongside businesses, charities, local government and the health sectors.
Ransomware Attacks
What is Ransomware?
Ransomware is a type of malware in which a cybercriminal encrypts or locks your data preventing access, holding your data for ransom.
Over half of ransomware attacks are targeting one of three industries; banking, utilities and retail, according to analysis by cybersecurity researchers – they've also warned that all industries are at risk from attacks.
Ransomware attacks against retailers can also have a significant impact, forcing shops to be restricted to taking cash payments, or even forcing them to close altogether while the issue is resolved, preventing people from buying everyday items they need.
The cybercriminal then threatens to publish sensitive data or permanently block access unless they are paid a certain fee anonymously through crypto.
To avoid paying hefty ransom fees, you should:
- Install and update your antivirus software.
- Backup crucial files and information.
- Avoid opening or downloading files or applications from unknown sources.
- Contact the relevant authority in case of a security breach.
OpenSubtitles.org members learned the hard way on January 18, 2022, when the website announced that a hacker gained access to the personal data of almost 7 Million users in August 2021, including email and IP addresses, usernames, and passwords.
OpenSubtitles bills itself as the “biggest multi-language subtitle database” online, with about 40,000 users during “peak” weekend hours, and a website available in more than 30 languages.
Users can upload or download subtitles without registering for the site, free registration gives members access to more advanced search functions and the ability to post comments on forums. For an annual rate of EUR 10, VIP members see an advertisement-free site and enjoy higher download limits.
According to Site Admin OSS, the hacker breached a Super-Admin’s account by hacking an unsecure password, thus gaining access to an unsecured script available only to OpenSubtitles Super-Admins.
The largest ransomware attack so far occurred in 2002, where the University of California paid $1 Million Ransom (£925,000) from a cyber attack alone.
3. Human Error Threats: Password Theft
No matter how secure your password is, unwanted third parties often find ways to guess or steal it, giving them access to sensitive data.
There are various ways you could protect your password from theft, including:
- Implementing multi-factor authentication.
- Using unique and robust password combinations with at least ten characters.
- Using password-less authentication, including fingerprints and facial recognition.
- Investing in a password manager.

Why password protect files?
If you share your PC or laptop with other people, say your family members, they’ll be able to see anything and everything you have on it including confidential or private stuff. Plus, there will always be a chance of human error: someone might delete or modify a file by mistake or accidentally share a private folder. Therefore, it is better to password-protect certain folders and files so that unwanted visitors can’t access them.
Protecting users from themselves
The largest issue faced by a remote IT team in keeping users safe and productive during the pandemic is keeping employees secure on a daily basis, according to 33% of system administrator respondents. Most of the IT professionals stated that the challenge originated from the shift from in-office to remote work when the COVID-19 pandemic set in and the lack of preparation time due to the quick shift.
Another big challenge comes with protecting employees against potential external threats. While workers were once safe behind the firewalls of their company’s in-office network, those layers of security have been lessened as workers are now utilizing personal and public networks that are typically not as secure.
Run a password audit
Having an online password manager is half the battle of securing your login info, but the other half is choosing strong passwords. The good news is that managing password health (as some services call it) is much easier with a password manager.
Most have a feature that not only verifies your passwords’ strength, but also checks to make sure they haven’t turned up in a data breach. If you find any website logins that need updating, changing them should be a snap, especially if you’ve got your password manager’s browser extension installed.
An ideal cybersecurity strategy should comprise cohesive security practices led by multi-faceted security solutions.
The following are a few examples of those security layers:
- Firewall - A firewall is the first line of defense for networks, protecting them from unauthorized access. The firewall analyses the requests and grants or denies access based on the provided rules. If any incoming traffic is flagged by the firewall, the access request is denied and blocked. Applications, networks and resources are all secured behind the firewall.
- VPN - A VPN is a security device that virtually establishes a private communication channel by connecting the user device to a secure server. When users access any network through a VPN, the data is encrypted and shared through a secure route, hiding the user’s IP and location.
- Email Security - Emails are still the most common form of communication in organizations, it’s absolutely essential to protect e-mail accounts and the data being shared from possible cyber threats.
- Password Security - Multi-factor authentication (MFA) is a practice which is core to the process of identity and access management, acting as the first layer of security. Pass-phrases that are difficult for the hackers to crack but easy for the user to remember can be used for additional password security in MFA.

4. Physical Threats: Social Engineering
Social engineering is a method of hacking that focuses on attacking the human element of a system.
While technology changes and grows, human nature reliably stays the same. For this reason, more and more hackers target the human part of the equation in a company’s security rather than the systems themselves.

Disruption in Operations
Social engineering attacks run far deeper than just social manipulation. They involve malicious programs and viruses that infect company devices and websites to spread infection.
Most attacks, if severe enough, make it impossible to simply go about your usual business day. Some level of maintenance and cleanup will be essential. However, certain attacks, specifically those that require a great deal of investigation, can destroy company productivity.
Education is probably the biggest step in the right direction. Ensuring that your team is fully informed and aware about how to deal with situations when faced with unfamiliar or suspicious messages is a must.

Impact on Reputation
The impact of social engineering on business starts with reputation. While a loss of company data can be devastating, few things are as difficult to recover as good faith from clients and trust. But how can hackers have such a radical effect on customer perception?
While almost any form of social engineering technique can damage reputation, we’ll focus on a few specific examples that have some of the most lasting consequences.

Financial Losses
Reputation and productivity are important, but companies operate for profit. Losing money can be one deadly impact of social engineering on business.
Any social engineering attack can cause a company financial losses. This is due to the selling of precious information on black markets, as well as the impacts that naturally come with losing public trust. If your clients lose faith in you due to a security breach and data loss, you’ll lose business. It’s as simple as that.

The effects of social engineering can go beyond lost files and stolen data. Various attack types can disrupt a company, cause financial loss, and result in a bad name for the organization.
That’s why it’s so imperative that you and your team are well-versed in preparing, identifying, preventing, and dealing with social engineering attacks.
Every organization should have protocols, standards, and guidelines in place to prevent your business from falling for social engineering attacks. Otherwise, the damage of such an attack can run rampant, and the effects on the company’s health can be catastrophic.

What is a Scareware Attack?
Have you ever received a pop-up notification warning that your computer has been infected with viruses? It’s a classic scareware technique. As its name suggests, a scareware attack scares users into thinking their computer has a virus. It baits them into a trap of downloading additional programs to remove the fake malware.
This type of cyber attack leverages pop-up ads and social engineering techniques. It encourages users to act fast to address a fake security issue.
The aim is to lure users into revealing sensitive information to what they think is a legit solution to their cybersecurity issue. Scareware attacks can cause several damages, including identity theft and credit card fraud. However, if you’re alert enough and know how to prevent scareware, you have nothing to worry about.
Top 4 Social Engineering Attack Techniques:
-
Baiting - Luring users into a trap that steals their personal information or inflicts their systems with malware.
-
Scareware - Users are deceived to think their system is infected with malware, prompting them to install software that is malware.
-
Pretexting - A social engineering attack that is often initiated by a perpetrator pretending to need sensitive information from a victims by impersonating co-workers, police, bank and tax officials, or other persons who have right-to-know authority
-
Phishing - Scams are email and text message campaigns aimed at creating a sense of urgency, curiosity or fear in victims.
Threat Prevention Tips Against Cyber Attacks
Increasingly, many employers are stepping up to the plate to train employees on how to identify and mitigate cybercrime threats. A good training program should cover topics such as:
- Avoiding the discussion of confidential information with third parties.
- Discouraging the practice of leaving sensitive documents on desks when not at work
- Avoiding the use of USB storage devices
- Sharing passwords or using easily guessed passwords
- Clicking on suspicious email links
- Conducting an audit by certified professionals

In addition, employers are beginning to initiate more vigorous background checks that investigate not only past criminal activity but also social media presence and other online behavior.
Another way IT professionals are addressing internal cybersecurity threats is by granting scaled network security access to employees based on their role within the organization and job function.
This type of graduated approach toward granting network access privileges is pivotal in making it more manageable to track which employees, if any, accessed certain areas of the network during a cyberattack or other security incident.
Managing internal security threats will always be a moving target, but the combination of a proactive and creative IT posture with ongoing employee training will go a long way toward crippling the efforts of nefarious actors bent on causing organizational disruptions and benefiting financially.

Cybersecurity is about equipping your business with the right technology and informing your employees on how to avoid falling into cyber traps.
Nobody is immune to the daily increasing cyber-threats. However, by raising awareness and using new technology, organizations can lower their risks. These tactics assist in protecting against a changing threat scenario.
How We Can Help
Despite their complexity, these methods are extremely cost-effective, adaptable, and easy to integrate. Furthermore, they are very user-friendly. In conclusion, you must decide what is best for your company, as every organization.
Learn how our certified professionals at CyberGuard Compliance can help educate, train and collaborate effectively with your business.


